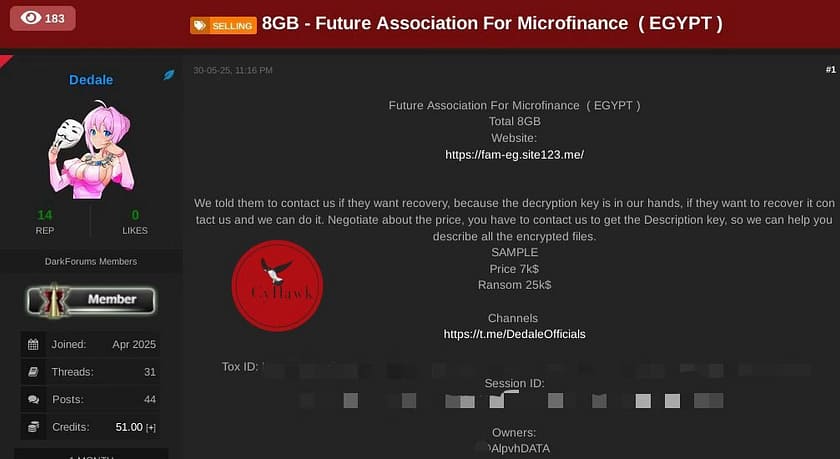
On May 30, 2025, a threat actor/group operating under the alias Dedale publicly claimed responsibility for a cyberattack on the Future Association for Microfinance (FAM), a nonprofit organization based in Egypt. In a post shared on a cybercriminal forum, Dedale announced they had stolen and encrypted 8GB of sensitive data from FAM and were demanding a $25,000 ransom for data recovery.
Dedale’s message included a sample offer priced at $7,000 and urged the organization to negotiate via their Telegram handle (@DedaleOfficials). Most notably, the post referenced the username @AlpvhDATA — a name clearly derived from ALPHV (BlackCat), a once-prominent ransomware group dismantled by law enforcement in early 2024.
Possible Ties to Nightspire and the ALPHV Ransomware Legacy
What makes this incident even more significant is its timing and stylistic similarities to activity observed earlier in the month. On May 6, 2025, the Nightspire ransomware group added a new victim to their leak site. Though they shared limited details, the operational timing and extortion approach suggest a pattern. See the post here.
Dedale’s choice of alias @AlpvhDATA, combined with his/their extortion format — multi-tier ransom pricing, public shaming, and Telegram-based communication — mirrors techniques used by former ALPHV affiliates and closely resembles Nightspire’s known playbook.
This raises the possibility that Dedale:
- Is an independent actor/group using tools or tactics learned from the ALPHV ecosystem
- Is collaborating with or operating alongside Nightspire, or
- Could be part of a broader network of threat actors formerly affiliated with ransomware-as-a-service groups now resurfacing under new identities