Egypt’s Maritime Transport & Logistics Sector (MTLS) has been at the center of a months-long cyber incident that continues to evolve, exposing 300GB of highly sensitive operational data and escalating the cyber risk to Egypt’s maritime infrastructure.
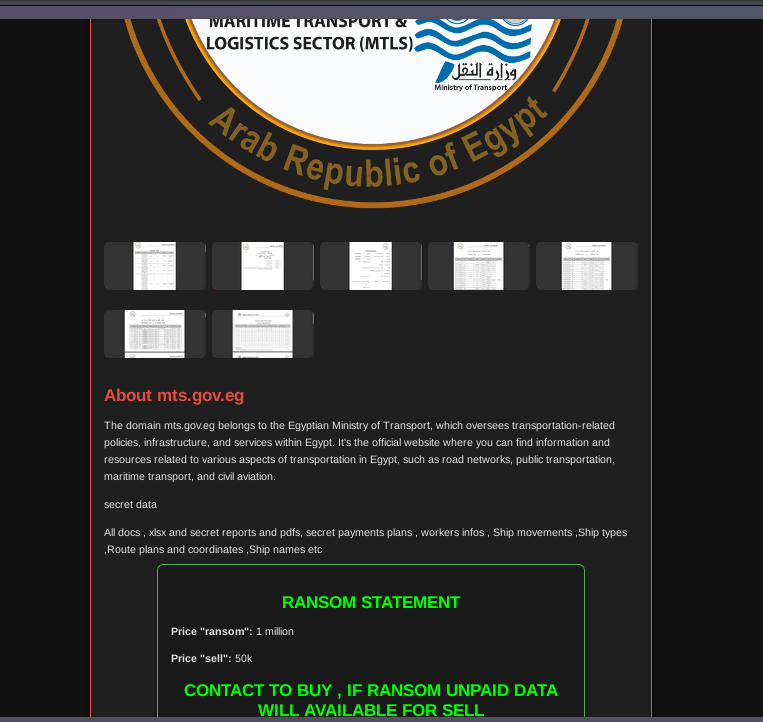
- January 15, 2025: The attack first surfaced when Funksec ransomware group demanded a $1 million ransom, threatening to leak stolen files from mts.gov.eg if unpaid. The data included:
- Secret payment plans
- Worker information
- Ship movements and ship types
- Route plans and coordinates
- Operational reports and maritime charts

- February 25, 2025: The dataset was later released by DarkForums admin Knox, with 300GB of data made publicly available for download after the ransom failed. The exposed materials included:
- Operational Reports
- Logistical Data
- Analytic Tables
- Internal Communications
- Maritime Activity Details
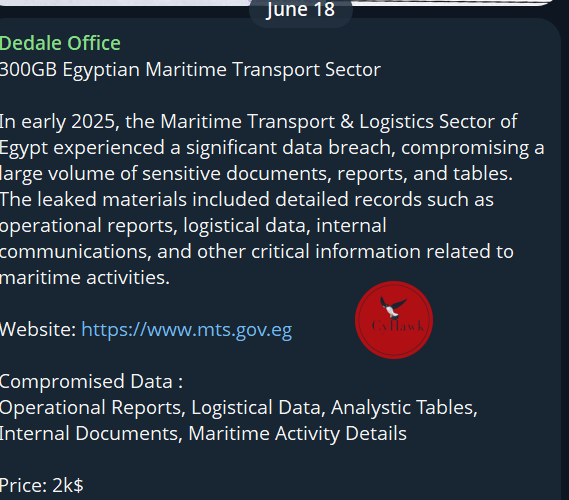
On June 18, 2025, the same dataset resurfaced on Telegram, where threat actor Dedale Office is now offering it for sale at $2,000, showing that the dataset is still being actively traded in cybercriminal channels.
This long-running exposure of Egypt’s maritime sector presents serious risks to commercial shipping, port operations, and national security. With operational data now widely accessible — from ship movements to port plans, malicious actors could disrupt maritime logistics, target vessels, or exploit weak points in Egypt’s maritime transport infrastructure.
The reappearance of this dataset in June, five months after the initial attack, highlights how ransomware and data extortion groups continue to profit long after attacks, circulating stolen data across multiple forums and Telegram markets.
Egypt’s transport and port authorities must urgently assess the exposure, patch vulnerabilities, and implement stronger incident response and data monitoring measures.
