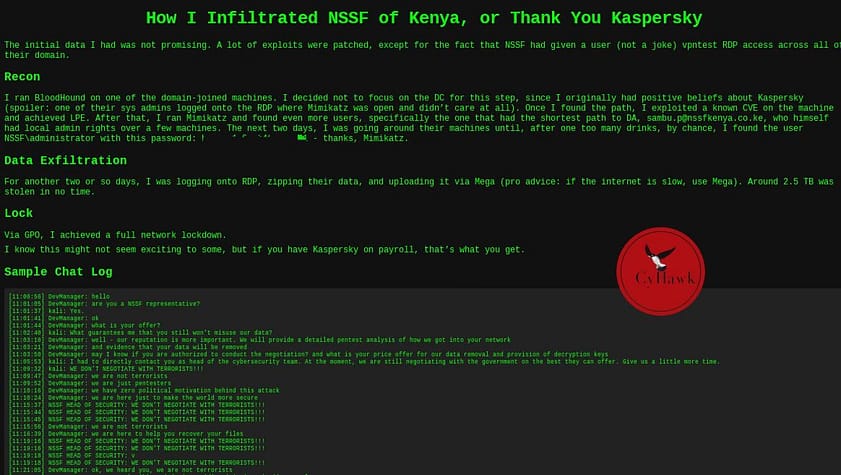
On May 19, 2025, Kenya’s National Social Security Fund (NSSF) was breached by the Devman ransomware group. It wasn’t until June 7, nearly three weeks later, that the group published a technical post on their dark web blog detailing how they pulled it off.
The post reads like a step-by-step manual, demonstrating how easy it can be for a skilled actor to navigate an unprepared environment. Using the MITRE ATT&CK framework, I broke down Devman’s operations to help security teams across Africa understand the tactics, techniques, and procedures (TTPs) used — and how to defend against them.

T1078 – Valid Accounts (Initial Access)
The breach began with something embarrassingly simple — a legitimate RDP account called “vpntest” that still had active domain access. This single oversight handed Devman their golden ticket into the network.
This scenario plays out repeatedly across organizations worldwide. Test accounts, service accounts, and temporary access credentials accumulate over time, often forgotten by IT teams until they become the very keys attackers use to unlock the front door. Regular access reviews and identity governance aren’t bureaucratic overhead — they’re critical security controls that could have prevented this entire incident.
T1482 – Domain Trust Discovery & T1087 – Account Discovery (Discovery)
Once inside, Devman deployed their reconnaissance toolkit. BloodHound helped them visualize Active Directory relationships and identify privilege escalation paths, while Mimikatz began harvesting credentials from memory. Their target was clear: find a path to Domain Admin privileges.
The combination of these tools in an under-monitored Windows environment is particularly devastating. BloodHound reveals the network’s crown jewels while Mimikatz provides the keys to access them. Organizations that haven’t hardened their Active Directory environments or implemented robust credential protection are essentially laying out a roadmap for attackers.
T1055 – Process Injection & T1003 – OS Credential Dumping (Privilege Escalation)
In what can only be described as extraordinary luck for the attackers, they discovered a system administrator had left a Mimikatz session running on their workstation. This provided direct access to privileged credentials, including the domain administrator account: NSSF\administrator.
This moment highlights a critical human factor in cybersecurity. Even security-conscious administrators can inadvertently create vulnerabilities through routine tasks. It underscores why privileged access workstations, session timeouts, and clean desk policies matter in high-security environments.
T1021.001 – Remote Desktop Protocol (Lateral Movement)
Armed with domain admin credentials, Devman used Remote Desktop Protocol (RDP) to hop between systems across the network. This technique remains effective in environments lacking proper network segmentation and behavioral monitoring.
Each RDP session gave them deeper access to sensitive systems and data repositories. The absence of alerts or restrictions on privileged account usage across multiple systems suggests NSSF lacked the monitoring capabilities needed to detect this type of lateral movement.
T1048 – Exfiltration Over Alternative Protocol & T1567 – Exfiltration Over Web Service (Exfiltration)
Over several days, Devman systematically compressed and uploaded 2.5 terabytes of NSSF data to Mega.nz cloud storage. Their own commentary about using Mega for “slow networks” suggests this wasn’t a rushed operation — it was methodical and patient.
The fact that this massive data transfer went undetected reveals gaps in Data Loss Prevention (DLP) controls and outbound traffic monitoring. Modern security operations should flag unusual upload patterns, especially when they involve compressed archives being sent to external cloud storage services.
T1486 – Data Encrypted for Impact & T1562.001 – Disable or Modify Tools (Impact)
Devman concluded their attack by pushing a Group Policy Object (GPO) that effectively locked down the entire network infrastructure. This ransomware-style tactic rendered NSSF’s systems unusable while the attackers attempted to negotiate.
Their demands came with a political twist — positioning themselves as “ethical hackers” seeking payment for a penetration test report and decryption key. NSSF’s response was unambiguous: “WE DON’T NEGOTIATE WITH TERRORISTS!”
This breach exposes deeper structural problems in cybersecurity practices across many organizations, particularly in developing countries. The attack succeeded not because of sophisticated zero-day exploits, but through the exploitation of fundamental security hygiene failures.
The Devman group’s success demonstrates how attackers increasingly rely on living-off-the-land techniques and publicly available tools rather than custom malware. They used legitimate system administration tools and protocols to achieve their objectives, making their activities harder to distinguish from normal administrative tasks.
Critical Takeaways
- Account Hygiene Matters: Test accounts, service accounts, and orphaned credentials are ticking time bombs. Regular access reviews and automated account lifecycle management aren’t optional — they’re foundational security controls.
- Assume Breach Mentality: Organizations must assume that tools like BloodHound and Mimikatz will eventually be used against them. This means implementing credential protection, privileged access management, and monitoring for these specific tools and techniques.
- Monitor What Matters: Unusual outbound traffic patterns, especially large file transfers to cloud storage services, should trigger immediate investigation. Data Loss Prevention isn’t just about preventing accidental data leaks — it’s about detecting deliberate exfiltration.
- Layer Your Defenses: Endpoint protection alone isn’t sufficient. Organizations need behavioral analytics, network segmentation, privileged access controls, and security operations capabilities that can detect and respond to multi-stage attacks.
As threat groups like Devman continue targeting public institutions across Africa and beyond, this incident serves as a stark reminder that cybersecurity isn’t just an IT problem — it’s an organizational resilience issue. The techniques used against NSSF are being deployed globally, and they’ll continue succeeding until organizations take proactive steps to address these fundamental vulnerabilities.
The question is not whether your organization could be targeted — it is whether you are prepared when that targeting inevitably occurs. The NSSF breach shows us exactly what that preparation should include.