CyHawk Africa has observed a widespread phishing campaign targeting financial institutions across multiple African countries, including Nigeria, South Africa, Egypt, and Kenya.
The campaigns leverage EvilProxy, an advanced Adversary-in-the-Middle (AiTM) phishing kit, and infrastructure operated by the Storm-1747 threat group, both of which are known for stealing credentials and bypassing Multi-Factor Authentication (MFA). Recent analysis indicates that each phishing URL is uniquely generated for individual targets, allowing threat actors to track user interactions and evade detection.
This campaign represents a strategic escalation of phishing activity against Africa’s financial sector, combining sophisticated lures, encrypted attachments, and dynamic AiTM infrastructure.
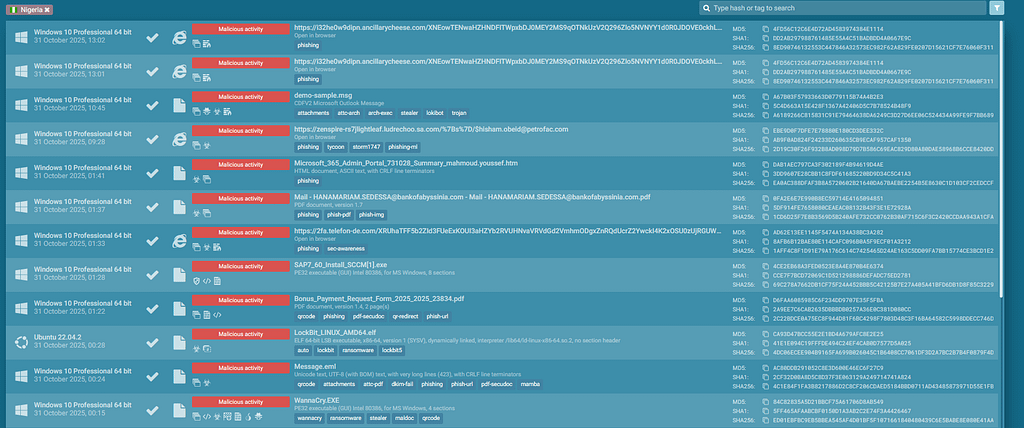
This coordinated activity marks one of the most significant phishing attack targeting the financial sector in Africa, combining password-protected email attachments with cloaked redirect chains to deliver highly convincing phishing portals.
Threat Overview
The phishing emails are typically themed around employee benefits, payroll updates, or account verification notices. Once opened, the attachment or phishing link displays a ” Cloudflare Verification” prompt and redirects through legitimate link-shortening or tracking services eventually landing on malicious domains hosted on Cloudflare.
These websites impersonate Microsoft 365 and other enterprise login pages, stealing credentials and session tokens in real time. After submission, victims are silently redirected to legitimate portals, concealing the compromise.
This campaign can be attributed to Storm-1747, a financially motivated threat actor known for operating the Tycoon 2FA and EvilProxy phishing kits under a Phishing-as-a-Service (PhaaS) model.
These affiliates sell access to these kits, enabling multiple criminal groups to run MFA-bypass phishing campaigns across different regions and industries. The current activity cluster is consistent with previous global EvilProxy operations, adapted to target African financial institutions.
Infrastructure and IOCs
| Type | Indicator |
|---|---|
| Domain | jinx.s-drc2.cloud.gcore.lu click.convertkit-mail2.com www.decifrando.net.br fiftheffectstudios.com koin777.store benefitsglobalportal.com elaineelstone.com www.srokkhmer.org www.contractorssupportshub.com clickboardingadvisor.com |
| IPs | 87.120.252.252104.21.16.149, 172.67.213.161 (Cloudflare CDN) |
| Phishing Kit | EvilProxy / Tycoon 2FA (Storm-1747 infrastructure) |
Note: Due to the campaigns’ use of unique, dynamically generated URLs, indicators may vary per recipient and should not be treated as exhaustive.
Technical Analysis
- The campaign uses Adversary-in-the-Middle (AiTM) phishing to intercept user credentials and MFA tokens.
- Each target receives a unique URL token (
?t=...), binding the phishing session to a specific recipient. - The use of password-protected attachments is intended to evade email gateway scanning.
- The domains are short-lived, rotated frequently, and hidden behind Cloudflare CDN to obscure origin servers.
Tactics, Techniques, and Procedures (TTPs) of the Phishing Attack
| Stage | Technique / Description | Detection Idea | Mitigation Step |
|---|---|---|---|
| 1. Reconnaissance | Threat actors gather public employee info (LinkedIn, websites) to craft HR or payroll-themed lures. | Watch for targeted emails to specific departments. | Limit exposure of employee data online. |
| 2. Delivery | Phishing email sent with either embedded links or password-protected attachments. | Flag emails with encrypted attachments or external links from unknown senders. | Quarantine encrypted attachments and force link previews. |
| 3. Social Engineering | Lure uses HR, payroll, or internal update themes to encourage clicks or attachment opens. | Spot similar subjects sent to many employees or HR-related messages outside HR teams. | Conduct targeted phishing-awareness training regularly. |
| 4. Redirection | Links redirect through multiple services to hide final destination. | Monitor proxy logs for multi-hop redirects. | Block link shorteners and apply safe link policies. |
| 5. Credential Harvesting | Landing page mimics real login page and captures credentials or MFA tokens. | Detect login attempts from unusual IPs soon after email click. | Enforce phishing-resistant MFA (FIDO2, security keys). |
| 6. Account Compromise | Stolen credentials used for unauthorized logins or BEC attempts. | Look for sudden location/device changes or suspicious mailbox rules. | Force password resets and revoke active sessions. |
| 7. Follow-on Actions | Access used for data theft, lateral movement, or ransomware staging. | Audit outbound mail and data transfers. | Isolate affected accounts and review permissions. |
CyHawk Africa Assessment
This campaign represents a significant rise in phishing targeting across the African financial ecosystem.
The combination of unique URL generation, MFA-bypass infrastructure, and password-protected attachments demonstrates a high level of operational maturity.
Given recent detections of both Storm-1747 and EvilProxy infrastructure, CyHawk Africa assesses that multiple threat actor groups or affiliates are collaborating to target African organizations, with goals ranging from credential harvesting to initial access for ransomware operations.
The use of PhaaS platforms like EvilProxy enables threat actors to scale operations rapidly across countries and institutions, making regional intelligence sharing and collective defense more critical than ever.
Recommended Actions
To protect your organization, CyHawk Africa advises the following:
- Block and monitor all known indicators (domains, URLs, IPs) in firewalls, email, and web gateways.
- Enforce phishing-resistant MFA (FIDO2/WebAuthn tokens) across all employee accounts.
- Implement attachment sandboxing for password-protected files.
- Conduct credential resets and session revocations for users who interacted with suspicious messages.
- Hunt for EvilProxy and Tycoon 2FA patterns in proxy and DNS logs.
- Restrict link-shortener access (e.g.,
app.linkila.com,bit.ly,tinyurl.com) in corporate environments. - Strengthen email authentication with SPF, DKIM, and DMARC enforcement.
- Raise awareness among employees on targeted HR and finance-themed phishing.
- Share indicators and findings with national CERTs and financial industry ISACs.
Conclusion
The ongoing phishing campaigns leveraging Storm-1747 and EvilProxy infrastructure mark a continent-wide escalation in targeted attacks against Africa’s financial sector.
By combining Adversary-in-the-Middle (AiTM) techniques, unique per-victim phishing URLs, and PhaaS distribution models, these campaigns enable attackers to bypass MFA, steal credentials, and prepare for potential ransomware or financial data theft operations.
CyHawk Africa urges all financial institutions, fintech companies, and digital service providers across the continent to tighten their security posture, adopt phishing-resistant authentication methods, and participate in regional intelligence-sharing initiatives to mitigate this growing threat.
Disclaimer: This advisory is based on open-source intelligence and verified CyHawk Africa investigations. The information is shared in good faith to raise awareness and support collective defense efforts across Africa’s cybersecurity ecosystem.

